For some reason you may need to route all the thaffic from your LAN through a tunnel to third-patry gateway. The tunnel encryption takes place on your router, which means it only applies to the traffic between your router and your VPN server. This guide will help you to set up a tunnel and routing correctly.
To have everything up and running you will need:
- OpenVPN server
- Internet access
- Mikrotik device
First of all you need a running OpenVPN server which you can connect to. It could be a private instance, in your datacenter or VDS. Also you can yse a tenant within public VPN provider. The main point is to have a routable IP address on your server and connection settings.
It is more comfortable to use *.ovpn profiles which contains all the setings and certificates you need to connect. ProtonVPN for example gives you such type of profiles.
Here you can find how to set up server and create client profiles. And here is a quick way. Also many VDS hostings will offer you a server template with pre-installed OpenVPN server.
Now its time to set up our router. I will use a HAP router, but for other mikrotik routers the procedure will be same.
- Open Winbox and connect to the router.
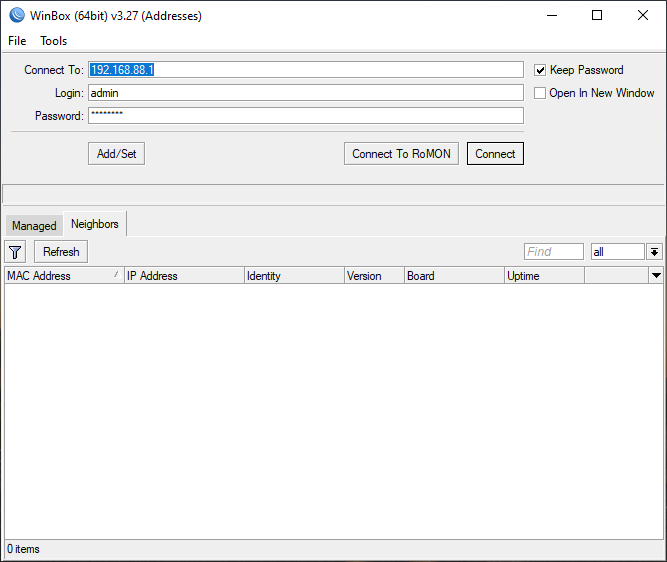
2. Open Files menu and upload *.ovpn client profile.
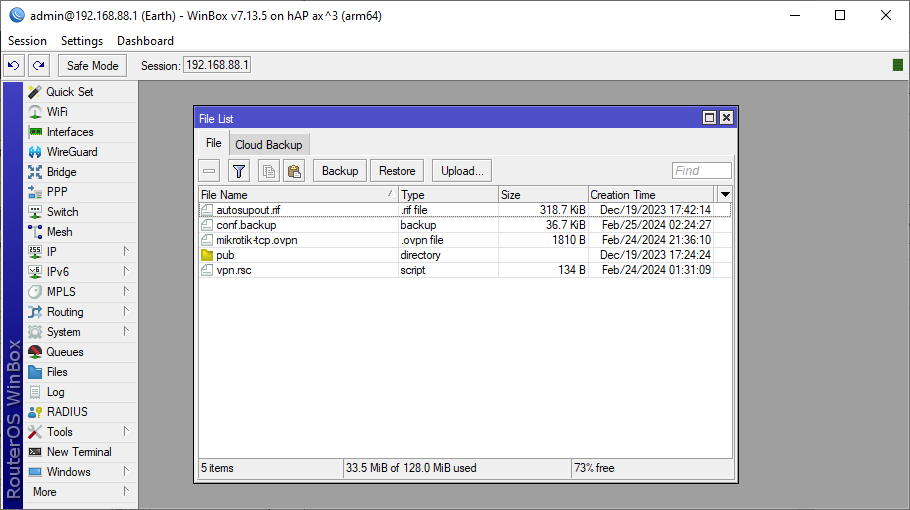
3. Go to PPP menu, click Import .ovpn and select profile you uploaded. After clicking Start, a new PPP Interface would be creted.
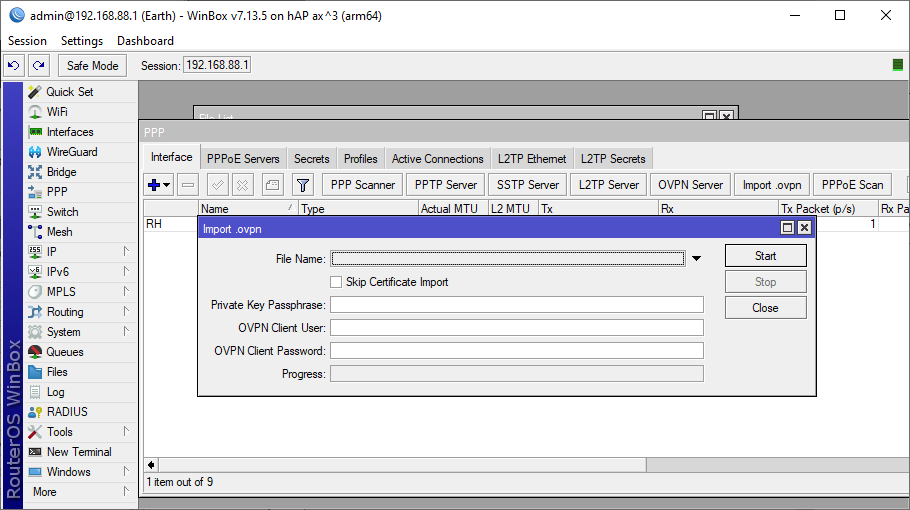
Then go to PPP > Interface, double click new interface, and select Dial Out tab. Here you will check that everything is imported correctly.
Review:
- Connect to: Server FQDN or IP
- Port: 1194 (according to server settings)
- Mode: tun or tap (according to server settings)
- Protocol: tcp or udp (according to server settings)
- Username and password: ProtonVPN profiles will require a correct username and password while your cusom installation may use authorization by client certificate. In this case you can enter any username and no password.
- Profile: could be left as default
- Certificate: from drop-down menu select your certificate that was imported with .ovpn profile.
- Verify server certificate: Yes
- TLS Version: only v1.2
- Auth: null. Note that RouterOS doesnt support tls-crypt for the moment. tls-auth should work, however I couldnt set it up, so I dont use it.
- Cipher: aes 256 gcm
- Use peer DNS: Yes
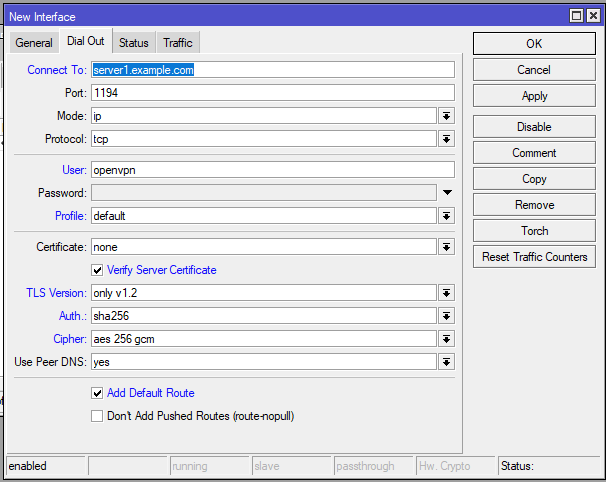
And here we go. After reviewing settings, click OK and enable this connection and all the traffic will now go through your OpenVPN server as a default gateway.
Currently there are many options where to deploy your OpenVPN server:
- In your datacenter
- Use a VPN provider which can offer you ready-to-use .ovpn client profiles. One of the most useful and non-expensive is ProtonVPN, a part of Proton services ecosystem.
- Deploy your OpenVPN on a virtual hosting.


Leave a Reply