Sometimes we need to connect to our infrastructure from the internet. Usually is is acheived with a tunnel between external device and on-site firewall if we have a routable IP on it. But sometimes we have a small standalone site where it will be tricky or costly to assign a routeble IP.
Today I willl tell about connecting to a site that is located behind a NAT.
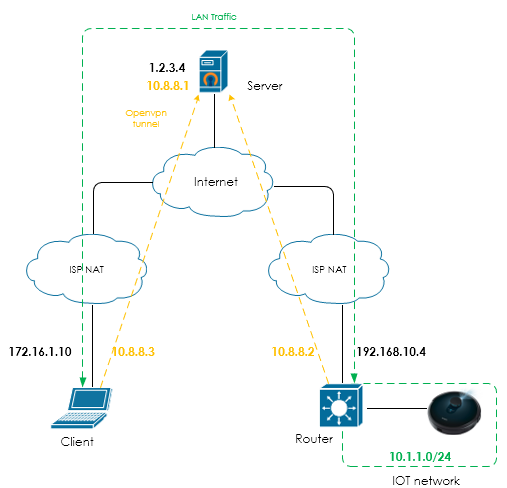
First of all, lets imagine we need to connect to IOT device on a small site. IOT network connected to the router, router connected to ISP. ISP want to save public addresses and places our router behind a NAT. This is how we have a private IP on our router WAN interface. At this point nobody can connect a tunnel to our router because our router doesnt have a globally routable IP. But a router can connect to some external host with public IP. It means that for creating a connection between two devices located behind ISP NATs we need an external routing device with public IP.
The concept is following.
- Client will connect to the external server
- Site router connects to the same server
- Server is forwarding traffic between client and router
For doing this first of all we need to obitain a server with public IP. You can order a virtual one here for 2$.
Next we have to setup a VPN server on new virtual server and create profiles for our devices. Angristan script can be used for this.
After we have a VPN server up and running we need to add a client-to-client setting in server config that will allow our client and router to communicate with each other via server.
Now, if everything is set correctly, our client can communicate with all the other clients of the server including router. But initial goal was to have access to all the networks connected to the router.
Let’s imagine we have a 10.1.1.0/24 network on site connected to the router. This network is not visible to the server, so to make server forward packets to this network we need to:
- Add a route to required networks in server’s routing table
- Add required networks to the client config
- Push route to these networks to the rest of clients
The route to network is a regular linux route. Can be created with command
ip route add 10.1.1.0/24 via 10.8.8.2After routing, packets will end up in a tun interface, which is actually Openvpn service. To define a network belonging to one of a clients, a file with client name (router in our case) have to be created in /etc/openvpn/ccd with following contents:
iroute 10.1.1.0 255.255.255.0Route will be pushed to all the clients if defined in openvpn config:
push "route 10.1.1.0 255.255.255.0"Openvpn config should look like this one:
port 1000
proto tcp
dev tun
user nobody
group nogroup
persist-key
persist-tun
keepalive 10 120
topology subnet
server 10.8.8.0 255.255.255.0
client-to-client
client-config-dir ccd
ifconfig-pool-persist ipp.txt
push "route 10.1.1.0 255.255.255.0"
push "dhcp-option DNS 1.0.0.1"
push "dhcp-option DNS 1.1.1.1"
push "redirect-gateway def1 bypass-dhcp"
dh none
ecdh-curve prime256v1
crl-verify crl.pem
ca ca.crt
cert server.crt
key server.key
auth SHA256
cipher AES-256-GCM
tls-server
tls-version-min 1.2
tls-cipher TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256
status /var/log/openvpn/status.log
#log /var/log/openvpn/openvpn.log
verb 3At this point we have everything working.
Useful links:

Leave a Reply