The concept
This topology may be unneeded and complicated in most of cases, however is it inspired by real life, so I will share it.
Let’s say you are sitting in one point of universe and have a WAN connection to your local ISP. For the same time you have an another location with another ISP and you want to appear to access some resource in the internet from location 2, while still sitting in location 1. How is this possible? Everything is possible after a good coffee.
The topology
First of all let’s imagine what do we have from network perspective. We have two locations each with it’s own LAN behind an ISP NAT. These locations cannot connect to each other, so we need a server with public IP.
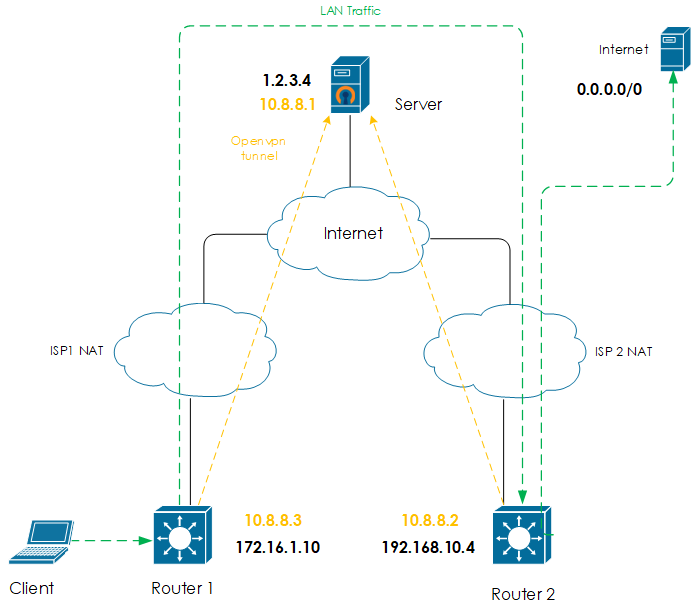
The server
For this purpose we can order a 4$ virtual server (for example here). We need to setup Openvpn on the server and create at least two config files. One for each location.
The routers
I will use Mikrotik routers running 7.x software as a border gateways for each site. Routers should be connected to openvpn server.
We are sending traffic from location 1 to the WAN link of location 2, so we need a router 1 connected to server as usual with default route leading to server.
Router 2 will receive traffic from Openvpn server through tunnel and use it’s default route provided from ISP for internet connection.
The configuration.
There are few important steps to make everything up and running.
First of all we need to connect each router to ISPs. Usually it is needed to set up a DHCP client on WAN interface
First router have to be connected to server and use tunnel as default gateway for all the clients traffic.
On server the following firewall rules have to be in place:
root@server:~# iptables -vnL
Chain INPUT (policy DROP 11893 packets, 529K bytes)
pkts bytes target prot opt in out source destination
20899 27M ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:1194
20899 27M ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:1195
22 2976 ACCEPT all -- tun0 * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- tun1 * 0.0.0.0/0 0.0.0.0/0
2647 293K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
30784 25M ACCEPT all -- tun1 tun0 0.0.0.0/0 0.0.0.0/0
30370 22M ACCEPT all -- tun0 tun1 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT 69639 packets, 53M bytes)
pkts bytes target prot opt in out source destination
root@server:~# iptables -vnL -t nat
Chain PREROUTING (policy ACCEPT 13177 packets, 628K bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 289 packets, 18132 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 2856 packets, 210K bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 982 packets, 75811 bytes)
pkts bytes target prot opt in out source destination
2579 199K MASQUERADE all -- * tun1 0.0.0.0/0 0.0.0.0/0 Next, Openvpn server configuration:
port 1194
proto tcp
dev tun0
user nobody
group nogroup
persist-key
persist-tun
keepalive 10 120
topology subnet
server 10.1.1.0 255.255.255.0
client-to-client
ifconfig-pool-persist ipp.txt
push "dhcp-option DNS 1.0.0.1"
push "dhcp-option DNS 1.1.1.1"
push "redirect-gateway def1 bypass-dhcp"
dh none
ecdh-curve prime256v1
crl-verify crl.pem
ca ca.crt
cert server.crt
key server.key
auth SHA256
cipher AES-256-GCM
ncp-ciphers AES-256-GCM
tls-server
tls-version-min 1.2
tls-cipher TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256
client-config-dir /etc/openvpn/ccd
status /var/log/openvpn/status.log
verb 3
log /var/log/openvpn/openvpn.logThis topology doesnt work on single Openvpn instance, so it is needed to create a second. This can be done by copying a server.conf to server2.conf. Openvpn will automatically recognize second config and create interface during next restart.
port 1195
proto tcp
dev tun1
user nobody
group nogroup
persist-key
persist-tun
keepalive 10 120
topology subnet
server 10.1.2.0 255.255.255.0
client-to-client
ifconfig-pool-persist ipp2.txt
#push "dhcp-option DNS 1.0.0.1"
#push "dhcp-option DNS 1.1.1.1"
#push "redirect-gateway def1 bypass-dhcp"
dh none
ecdh-curve prime256v1
crl-verify crl.pem
ca ca.crt
cert server.crt
key server.key
auth SHA256
cipher AES-256-GCM
ncp-ciphers AES-256-GCM
tls-server
tls-version-min 1.2
tls-cipher TLS-ECDHE-ECDSA-WITH-AES-128-GCM-SHA256
client-config-dir /etc/openvpn/ccd
status /var/log/openvpn/status2.log
verb 3
log /var/log/openvpn/openvpn2.logRoute configuration.
The most important thing here is a routing performed on server. For proper traffic forwarding we need a custom routes and rules in place.
ip route add default via <server public ip> table 5
ip rule add from <server public ip> lookup 5
ip route add default via <site 2 tunnel ip> table 5First command to add a default route to custom routing table.
With secoond we switch the table that is applied to packets entering server’s interface. Required for proper VPN and SSH working.
Third command to switch server’s default gateway to site 2. Site 2 ip is IP assigned to openvpn interface on router 2.
Router 2.
At this point we have a client’s traffic forwarded from Router 1 through Server to Router 2.
Finally it is needed to add a masquerading rule on Router 2 to send all the traffic originating from tunnel to router’s default gateway, which is ISP provider.
Useful links:
- https://hamalaon.com/how-to-set-up-mikrotik-openvpn-client/
- https://hamalaon.com/overcoming-isp-nat-with-virtual-server/
- https://linuxopsys.com/permanently-add-static-route-in-linux
- https://www.mybluelinux.com/debian-permanent-static-routes/
- https://forums.openvpn.net/viewtopic.php?f=30&t=22603
- https://forums.openvpn.net/viewtopic.php?t=31243
- https://www.hugeserver.com/kb/openvpn-multiple-ports/

Leave a Reply